Coauthored with Dr. Randall Minas, University of Hawaii at Manoa and Presented at Human Computer Interaction International 2020
As of writing this, I have yet to conduct the experiment due to COVID-19. I intended to conduct it right after Spring Break, but we never returned. Now I am in the midst of my Dissertation, so will need to balance that and finishing this. Hopefully I can finish this soon. I enjoyed coming up with the experiment and hope it has some lasting impacts for understanding technostress individuals and how interruptions can impact performance.
Abstract. The prevalence of information systems and the resulting increase in continuous notifications have blurred the lines of work and leisure, resulting in increased stress. These changes in the work environment have had detrimental effects on workers ability to sustain attention and remain productive. Despite academic interest in both IT-mediated interruptions and technostress, there has been little research on the juncture of both of these while also utilizing eye tracking. We propose an experimental design on a sampling of undergraduate students in order to study the relationship of IT-mediated interruptions on task performance and the moderating effect of technostress on this relationship. In addition to we will utilize eyetracking (pupillary dilation and gaze duration) to tie the level of
IT-mediated interruptions to cognitive resources in low and high technostress individuals.
Research Model
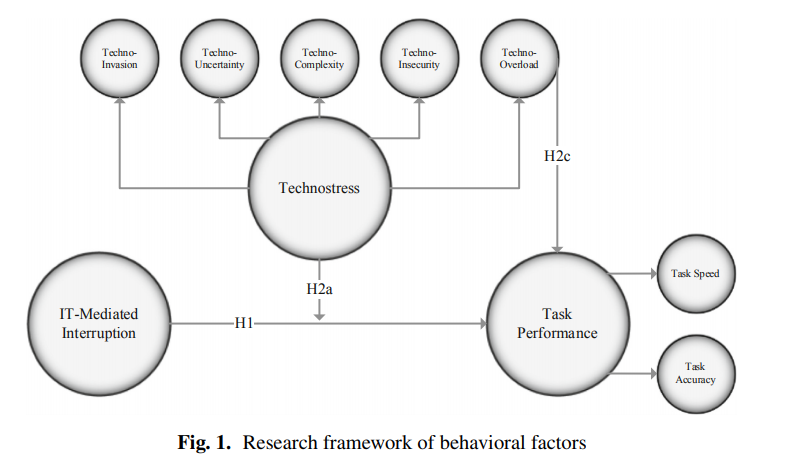
Link to Paper
Link to Official Site
Link to Presentation (sorry for recording the wrong portion of the screen)