In the last tutorial, we learned about configurable joints, anchors, XYZ Motion, Angular XYZ Motion, Angular XYZ Limits, Target Rotation and Angular Velocity, as well as, Angular XYZ Drives.
In this lesson, we are going to learn how it works when connected to one or more other configurable joints to start to create a body. The final tutorial will go over configuring a rigged character and making it stand and balance. So let’s get started.
Rename our Cube to Forearm. Press Ctrl+D or right click and click duplicate. Rename this to Upper Arm and drag the green arrow directly up to look below. Leave a little space so we can see the rotations a bit better. If we just press play, the joints act like the aren’t connected and will both swing like how we set up our forearm.
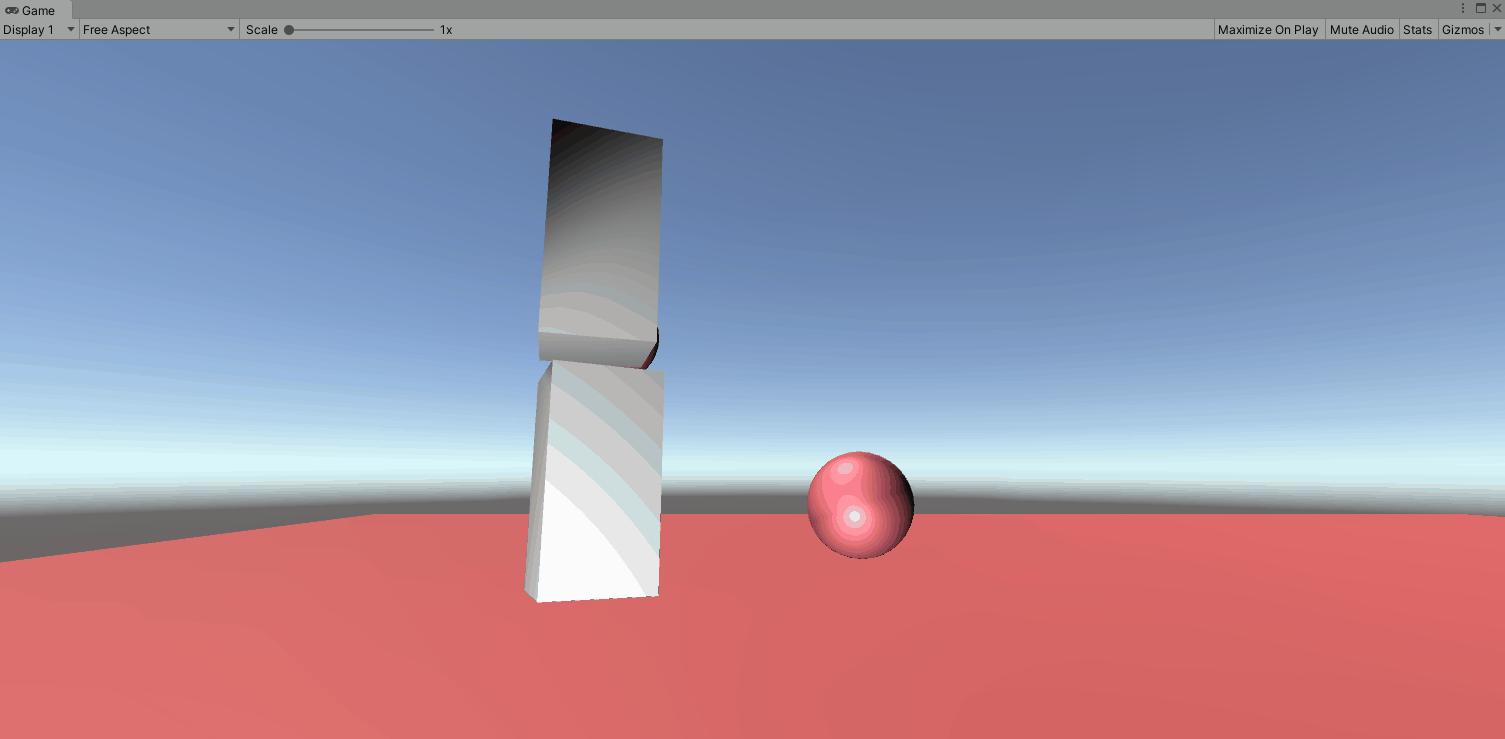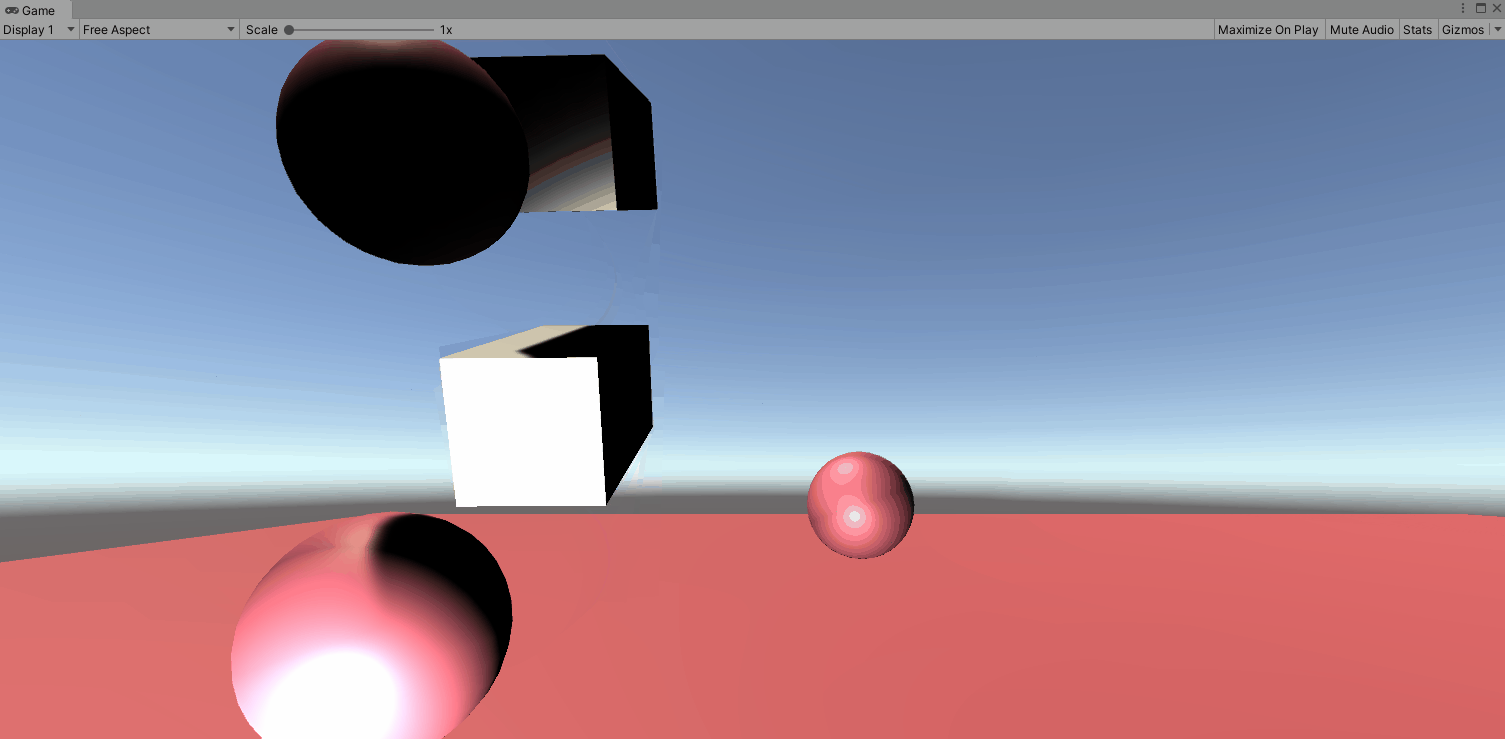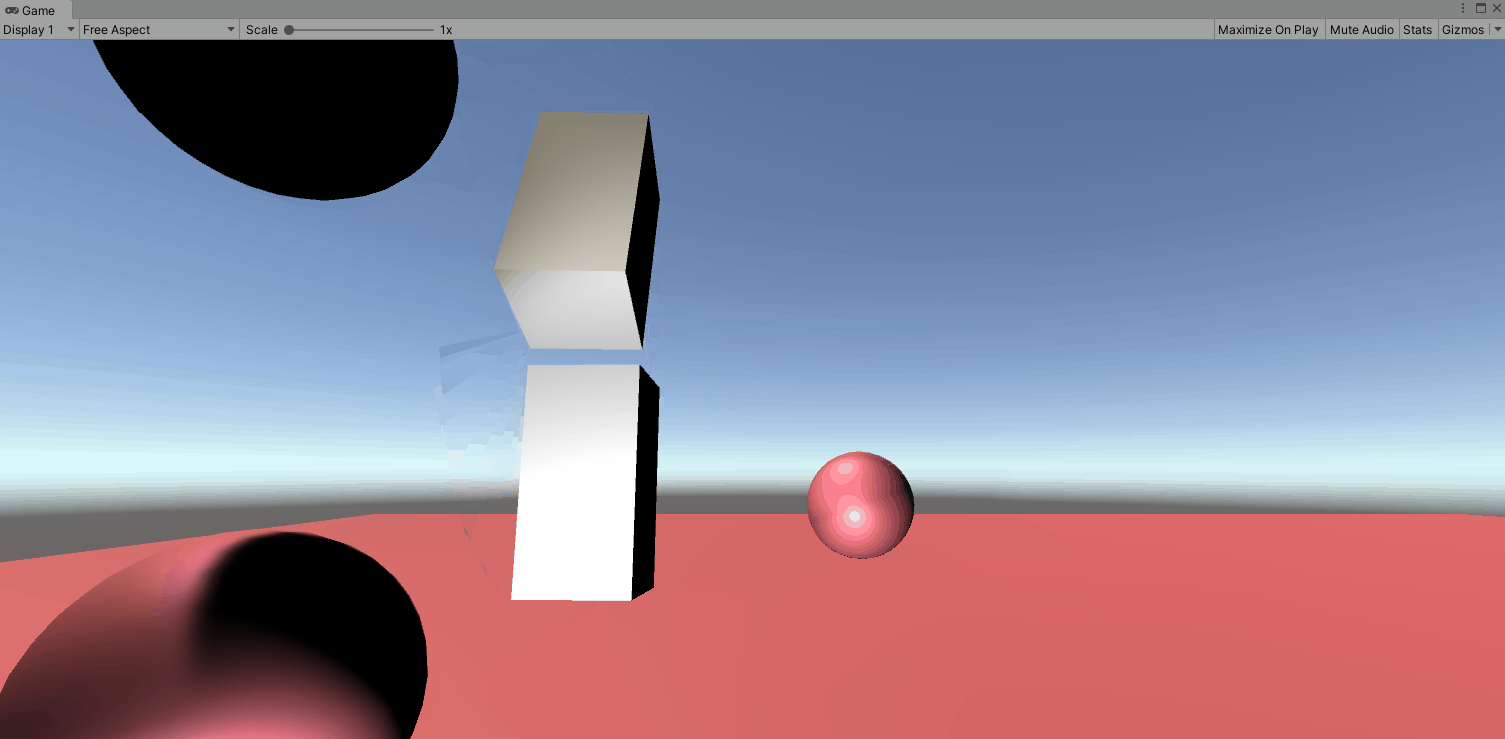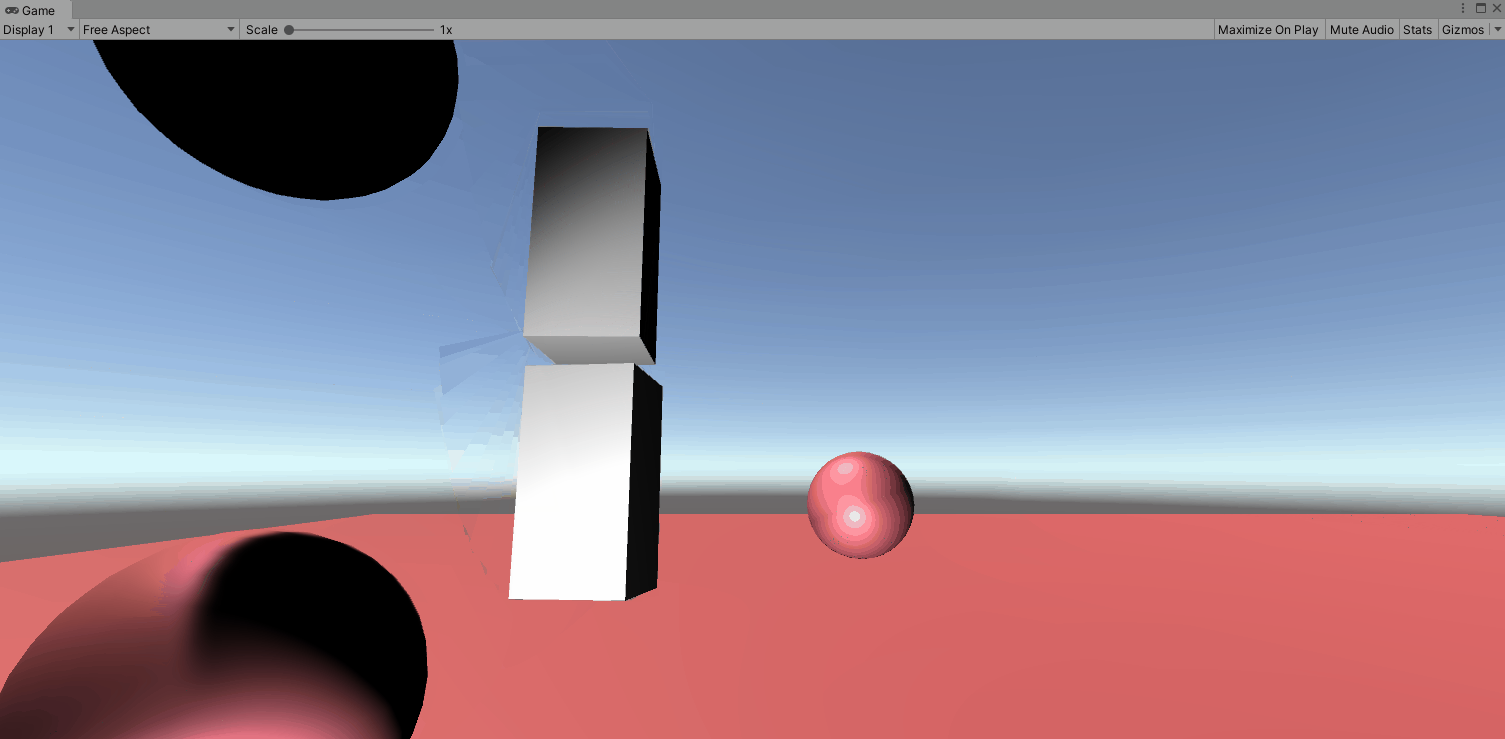
Next we are going to reset the configurable joint to our elbow. Right click the upper arm and click reset. First we want to lock the XY and Z motions as we don’t want it to move laterally. Next we want to look closer at the connected body. If we drag the ForeArm rigidbody to the Upper Arm we get the below. Not what we are going for. In this case it looks like the top of the forearm is connected to the top of the upperarm by an imaginary line. So they rotate around themselves. (for the purpose of this gif, i locked the Y and Z axis on the upperarm).